고정 헤더 영역
상세 컨텐츠
본문
I recently read a hint about enabling email over ssh. I've been trying to set that up on Mac OS X since I switched (from OS 9), but I always received an odd error, and it never worked, no matter how much research I did, and how many different options I tried. It worked for tunneling ftp, http, and all sorts of other protocols.
It's a straight-forward setup: ssh -CN -L 2025:mail.isp.com:25 -L 2110:mail.isp.com:110 myshortname@localhostThen set Mail.app to use localhost as the SMTP and POP3 servers, and set the ports to 2025 and 2110 respectively. Oh well, for some reason, now it works. Which lead me to try to discover a way of automating the task when my user account logs in. I could make a /Library/StartupItem, but that would run even when my user wasn't logged in - that's not what I want. I could make an alias in my shell, then open up the Terminal and type the alias every time - that's too much work. I could create a shell script text file and name it mailtunnel.command and add it to my user account startup items.
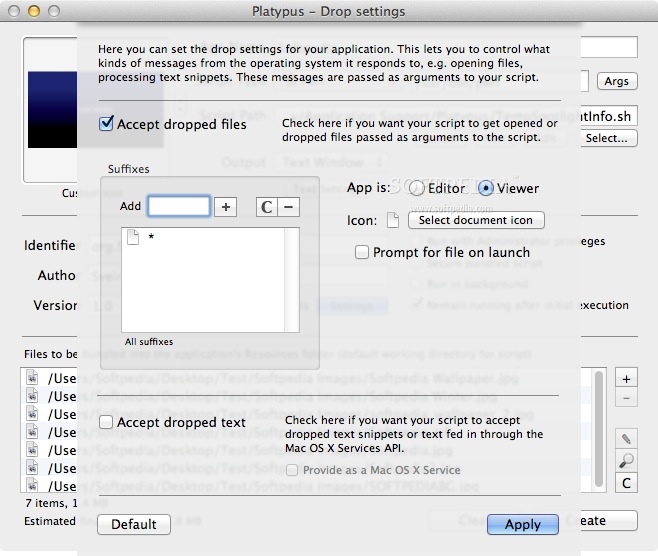
That's messy because it opens up the Terminal.app and leaves the window open. I could have a contextual menu or open a special application that I could use to select a shell command that would trigger the command without Terminal.app opening. That's still too much work. I don't want to have to do anything. Read the rest of the hint for my solution. After some searching, I found a fantastic application called. From their website: Platypus is a powerful developer tool for creating application wrappers around scripts, i.e.
For creating MacOS X applications that execute a bundled script. Scripts can thus be run seamlessly from the graphical window environment, making elegant Mac OS X-native applications from scripts. Doesn't have to be tiger. Here is the short and simple for creating a public key 1.
On your local computer, open a terminal 2. Type `ssh-keygen -t rsa` 3. The following prompt comes up: Generating public/private rsa key pair. Enter file in which to save the key (/home//.ssh/idrsa): 4.
Accept the default (it's in your home directory) 5. Leave passphrase field blank twice Enter passphrase (empty for no passphrase): Enter same passphrase again: 6.
You will get something similar to the following output Your identification has been saved in /home//.ssh/idrsa. Your public key has been saved in /home//.ssh/idrsa.pub. The key fingerprint is: a6:ca:aa:c7:fb:db:93:77:1d:da:07:c1:99:7c:3f:db @yourcomputer.com 7. This has created a directory, in your home directory named '.ssh' 8. `cat.pub` This will print to the terminal the contents of your public key. This is what you want to put on any remote server that you want passwordless login to.
Copy the output 11. Login to the remote server 12. If the.ssh dir does not exist in your home directory on the remote server, create it.
Fish For Mackerel Block Island
Type the following: echo ' authorizedkeys 14. You should have pasted the previously copied contents in between the single quotes. Logout, and try logging back in. It should not ask you for a password. If you have a newer system, you might need an authorizedkeys2 file In summary, for all systems that you want to login to, you copy the contents of /.ssh/idrsa.pub into the authorizedkeys file the authorizedkeys file can contain multiple keys, so that you can login to it from many different systems. While you can copy the.pub file to many different systems, i recommend that you do NOT copy the private key (idrsa) to any other system on any system that you are going to login FROM, create a key, and copy the public key (.pub) to the systems you are going to login TO. And yes i know you can do some of this in a more streamlined manner, but this explains exactly what is going on, and what goes where.
One might use SSHKeyChain for this. It stores your secret key's password, and as an extra bonus it has the ability to easily dig secure tunnels for you. By the way, are you sure your setup is secure? You connect to localhost via ssh, and then forward some ports to a remote machine. I wouldn't be surprised if forwarding would be insecure this way I would do something like the following: ssh login@ssh-server.isp.com -L 10110:mail.isp.com:110 This way the connection to your isp's ssh-server is secure, and maybe the last bit from ssh-server.isp.com to mail.isp.com is not, but that's no problem. 'Perhaps nothing is quite true, and not even that!'
Multatuli, Ideen 1. Ok, time for the responses: 1. I do use password-less SSH 2-DSA keys (I use, for key generation and management, great app), all of my machines that have password-less keys are physically secure. I screwed up in my explanation. My office box is on a LAN behind a separate firewall box, my mail server box is on a different LAN behind another separate firewall box (gotta love old blue and white G3 towers) and the two LANs are separated by the intarweb.
Platypus Macquarie
I actually tunnel from my office box through the remote firewall (where I have login access), straight to the mail server. Office Workstation - Firewall - Intarweb - Firewall - Mail Server Even though I'm a retard and screwed up the part about sshing, the point that I was trying to make, was that: Platypus is a great solution for getting command line scripts or programs to run without any interface at user login (and it does so much more). Please accept my sincere apologies for being a moron on the path to making my ultimate point.




